Fraud Management & Cybercrime , Ransomware
Check Point Research: Operators of 'Black Rose Lucy' Malware Add Capabilities
The gang behind Black Rose Lucy malware, which targets Android users, has added ransomware capabilities, according to Check Point Research. The malware, which dates back to 2018, originally was designed as a malware-as-a-service botnet and dropper for other malicious code but has now expanded.
See Also: Role of Deception in the 'New Normal'
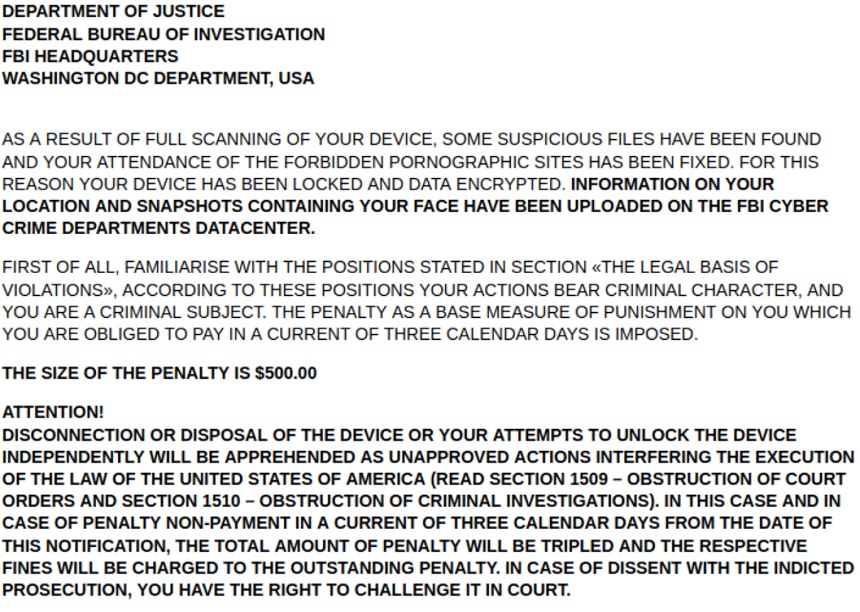
The new ransomware capabilities encrypt files and data on infected Android devices, according to a Check Point Research report. The malware then sends victims a note through a web browser that claims to come from the FBI. These ransom notes claim the victim visited "forbidden pornographic sites" and that this data is being encrypted and transferred to an FBI database, the report states.
The ransom note adds that victims need to pay the $500 penalty within three days or face further legal consequences, the report notes. This fine can be paid through a credit card, which is a change from the usual methods of extorting victims by having them pay a ransom with cryptocurrency such as bitcoin.
The shift to mobile ransomware is part of a small, but growing trend among some cybercriminals to take advantage of mobile devices that tend to have fewer security features, according to the Check Point Research report (see: Mobile Ransomware Targets Android Users Through SMS).
"Mobile ransomware is getting more and more sophisticated and efficient, as shown by Black Rose Lucy, and this represents an important milestone in the evolution of mobile malware," the report notes.
Mobile Ransomware
The malware, which appears to have originated in Russia, is known to spread through social media links as well as instant messaging apps, according to the report. Check Point researchers have recently found 80 variants of the malware in the wild, including versions that incorporate ransomware elements into attacks.
If a victim picks up a malicious link from a social media site or instant messaging apps that is disguised an invitation to view a video, the malware displays a message on the Android device asking the user to enable streaming video optimization to watch the video, according to the report.
If permission is granted, the ransomware then targets the device's Android Accessibility Services, a feature that Google built into its mobile operating system to help users with disabilities by automating certain features. By controlling this feature, the attackers can bypass security tools and gain near-total control of the device, according to the report.
"Accessibility services are normally used to allow users to automate and simplify certain repeated tasks," according to Check Point. "With Lucy, it's the Achilles Heel in the Android's defensive armour."
The researchers noted that the malware connects to a command-and-control server, but the new versions of Black Rose Lucy use a domain to communicate with the attackers rather than an IP address.
Once the malware infects an Android device, it starts looking for directories in the smartphone's main storage as well as the SD card, and then begins encrypting files. After it checks that all the files are crypto-locked, it sends the spoofed FBI message to the victim depending the $500 payment, the report notes.
Microsoft has reported that over the past two weeks, it has seen 10 ransomware families used frequently (see: 10 Ransomware Strains Being Used in Advanced Attacks).
"Android" - Google News
April 30, 2020 at 02:55AM
https://ift.tt/3aQsWD3
Fresh Ransomware Targets Android Devices - BankInfoSecurity.com
"Android" - Google News
https://ift.tt/336ZsND
Shoes Man Tutorial
Pos News Update
Meme Update
Korean Entertainment News
Japan News Update
Bagikan Berita Ini














0 Response to "Fresh Ransomware Targets Android Devices - BankInfoSecurity.com"
Post a Comment