
More than 4,000 Google Play apps silently collect a list of all other installed apps in a data grab that allows developers and advertisers to build detailed profiles of users, a recently published research paper found.
The apps use an Android-provided programming interface that scans a phone for details about all other apps installed on the phone. The app details—which include names, dates they were first installed and most recently updated, and more than three-dozen other categories—are uploaded to remote servers without permission and no notification.
IAM what IAM
Android’s installed application methods, or IAMs, are application programming interfaces that allow apps to silently interact with other programs on a device. They use two methods to retrieve various kinds of information related to installed apps, neither of which is classified by Google as a sensitive API. The lack of such a designation allows the methods to be used in a way that’s invisible to users.
Not all apps that collect details on other installed apps do so for nefarious purposes. Developers surveyed by the researchers behind the new paper said the collection is the basis for launcher apps, which allow for the customization of the homescreen and provide shortcuts to open other apps. IAMs are also used by VPNs, backup software, notification managers, anti-malware, battery savers, and firewalls.
But the data grab can also be used by advertisers and developers to assemble a detailed profile of users, the researchers reported in their paper, titled Leave my Apps Alone! A Study on how Android Developers Access Installed Apps on User’s Device. They cited previous studies such as this one, which found that a single snapshot of apps installed on a device allowed researchers to predict the user’s gender with an accuracy of around 70 percent. Follow-on findings by the same researchers expanded the demographics that could be deduced to traits such as religion, relationship status, spoken languages, and countries of interest. A study by different researchers said user demographics also included age, race, and income. The research also found that a user’s gender could be predicted with an 82 percent accuracy rate.
“As other privacy-sensitive parts of the Android platform are protected by app permissions, forcing developers to explicitly notify users before attempting access to these parts, [it] begs the question on why IAMs are treated differently,” the researchers, from the University of L’Aquila in Italy, Vrije University in Amsterdam, and ETH in Zurich, wrote in the latest paper. “Indeed, the European Union General Data Protection Regulation (GDPR), generally regarded as the forefront in privacy regulations, considers ‘online identifiers provided by their devices, applications, tools, and protocols’ [...] as personal data, for all purposes and means.”
Changes
The new report said that Google is considering several changes to Android that have already been added to a beta version of version 11 (general release has been scheduled for the third quarter, but it’s not clear if that timeframe will be pushed back as a result of disruptions caused by the COVID-19 pandemic). Under the considered change, for an app to interact with other apps, the developer must either (1) explicitly declare in the app manifest—a file that describes essential information about the app—the apps they want to inspect or (2) require a new permission called QUERY_ALL_PACKAGES, whose precise function remains unclear to some developers.
The change, the researchers said, still doesn’t address one of the chief shortcomings of the IAMs abuse, which is the lack of notice to users that an app requires a potentially privacy-invading permission. Under the considered change, apps still wouldn’t be required to disclose their collection of details about all other installed apps. Google representatives didn’t respond to an email inquiring about planned changes in Android and requesting a more general comment for this article.
App spying
The researchers studied 14,342 free Android apps in the Google Play Store and 7,886 open source Android apps and analyzed the apps’ use of IAMs. The researchers found that 4,214 of the Google Play apps, representing slightly more than 30 percent of those studied, used IAMs. Only 228 of the open source apps, or a little less than 3 percent, collected details of other apps. With more than 3 million apps available in the Google-hosted service, the actual number of prying apps is almost certainly an order of magnitude higher than the 4,214 found in the study.
In descending order, the top five Google Play app categories that most frequently collected the data were: Games (73 percent), Comics (71 percent), Personalization (61 percent), Autos and Vehicles (54 percent), and Family (43 percent). The figure below lists the use of IAMS across all categories.
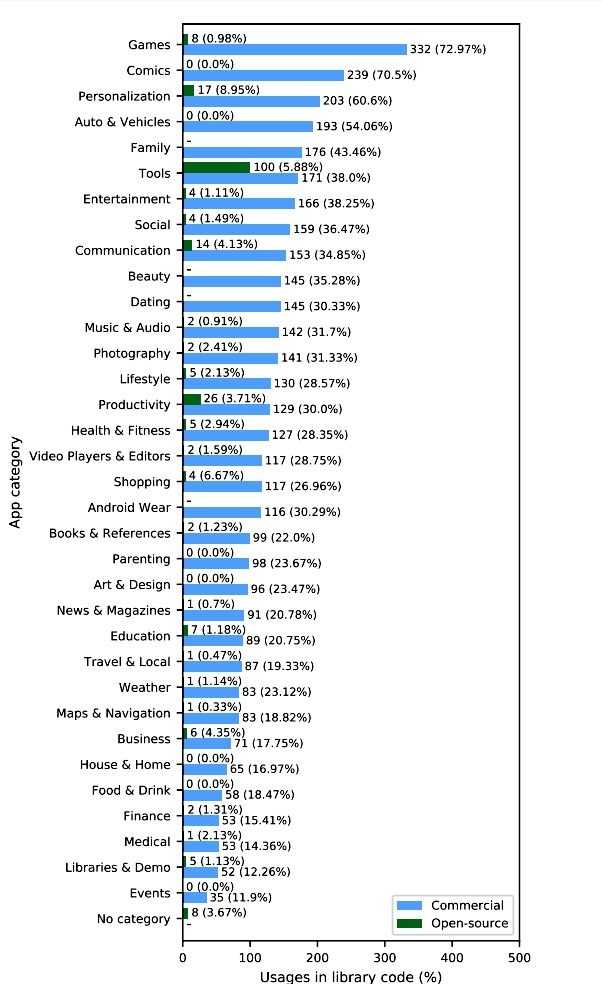
The paper didn’t identify any of the apps by name.
The vast majority of the Google Play apps that collected app data—84 percent—did so using third-party code libraries. The researchers identified 56 ad libraries that collected the data and found that a “small number” of them accounted for more than a third of all IAMs usages by bundled libraries. Other bundles identified were utility libraries, custom libraries, and analytics and app-promotion libraries. Below is a table listing the top 20 most common libraries:
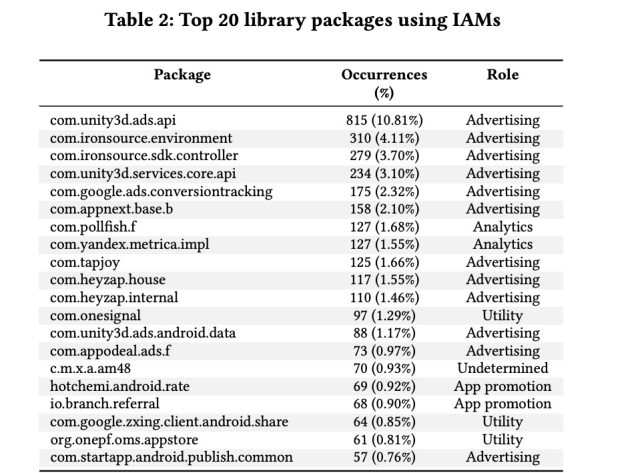
“In the discussion of results, we assumed that [the] vast majority of the IAMs calls performed by advertisement libraries are for profiling purposes, and we therefore suggested some potential changes to the Android platform accordingly,” the researchers wrote. Chief among the recommendations was that users receive notification that an app is requesting permission to access other installed apps. Like other permissions requests, it should give users the ability to refuse.
The researchers said Apple’s iOS uses methods similar to IAMs to allow apps to track other installed apps. The researchers went on to say that in recent versions of the OS, “applications of interest have to be preemptively declared inside the app... manifest file, and thus are reviewed by app store moderators before publication.”
As noted earlier, there are legitimate reasons for apps to collect details of other installed apps. But there’s also reason for concern. This latest research only reinforces the advice I’ve long given that Android apps should be installed sparingly and only when they provide a clear benefit. It also helps to favor fee-based apps over free ones, since the latter category is more likely to depend on advertisements for revenue. Open source apps are also shown to collect less app data, but they also require users to allow installations from third-party marketplaces.
"Android" - Google News
March 28, 2020 at 10:41PM
https://ift.tt/2Us5veu
4000 Android apps silently access your installed software - Ars Technica
"Android" - Google News
https://ift.tt/336ZsND
Shoes Man Tutorial
Pos News Update
Meme Update
Korean Entertainment News
Japan News Update
Bagikan Berita Ini














0 Response to "4000 Android apps silently access your installed software - Ars Technica"
Post a Comment