DDoS Protection , Endpoint Security , Internet of Things Security
Researchers: 'Matryosh' Designed to Support DDoS Attacks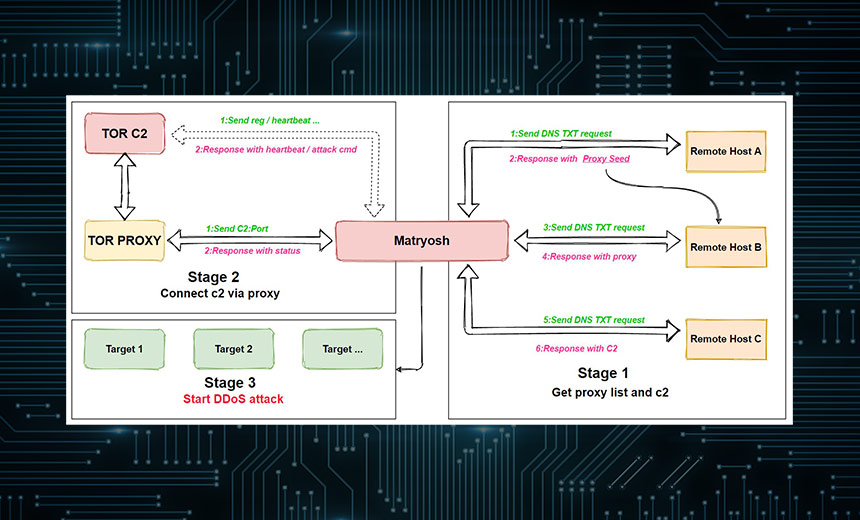
Researchers at the security firm Netlab have identified a previously undocumented botnet dubbed "Matryosh" that is targeting vulnerable Android devices to help build its network so it can conduct distributed denial-of-service attacks.
See Also: 2021: The Cyber-Attack Outlook
The Matryosh botnet, which the researchers discovered Jan. 25, looks for Android devices in which the smartphone manufacturer left the Android Debug Bridge feature - a diagnostics and debugging tool - unsecured and open to the internet, the report notes.
Other botnets are also taking advantage of the Android Debug Bridge feature when the tool is left unsecured. For example, in October 2020, Barracuda Networks discovered a botnet called "InterPlanetary Storm" that followed a similar pattern (see: 'InterPlanetary Storm' Botnet Infecting Mac, Android Devices).
Burak Agca, an engineer at the security firm Lookout, notes more hackers are taking advantage of the unsecured Android Debug Bridge tool because it opens the door to connecting to a device, installing apps and executing commands - all without authentication.
He advises organizations using Android devices to implement mobile device management systems to ensure that features such as Android Debug Bridge are turned off or are secured when malicious payloads are detected.
Unique Features
The Matryosh botnet contain some features not typically found in most other botnets, the NetLab researchers say.
Among these are the use of the anonymous Tor network to help hide the command-and-control servers from security tools. The botnet's operators have also created a multistep process for the malware to obtain the address of the command-and-control server, which also further hides its activities.
"The changes at the network communication level indicates that its authors wanted to implement a mechanism to protect [command and control]," the researchers note.
The researchers believe that Matryosh is mainly designed to start DDoS attacks over ports such as TCP, UDP and ICMP.
The Netlab report also notes that Matryosh appears to be related to botnets developed by a hacking group called Moobot, which has been active over the last few months. For example, one of the group's botnets, LeetHozer, also uses the Tor network.
Mirai Connection?
The Netlab researchers say that when they first discovered Matryosh, they believed it was a revamp of the notorious Mirai botnet. A closer look at the network traffic, however, found that Matryosh was a separate botnet, but it appears to use some of the same source code as Mirai.
Mirai is best known for its use in a massive DDoS attack that took down large portions of the internet in October 2016. While three of Mirai's co-authors were eventually convicted and sentenced for creating the botnet, the code they used remains available for other cybercriminals to modify for their purposes (see: Mirai Botnet Code Gets Exploit Refresh).
"Android" - Google News
February 06, 2021 at 01:18AM
https://ift.tt/2MZJaDL
Recently Uncovered Botnet Targets Android Devices - BankInfoSecurity.com
"Android" - Google News
https://ift.tt/336ZsND
https://ift.tt/2KSW0PQ
Bagikan Berita Ini
















0 Response to "Recently Uncovered Botnet Targets Android Devices - BankInfoSecurity.com"
Post a Comment