Holy floppin' hellfire, Henry! Have you heard? A terrifying new form of Android malware is running amok — stealing passwords, emptying bank accounts, and drinking all the grape soda from the refrigerators of unsuspecting Android phone owners.
We should all be quivering in our rainboots, according to almost all the information I've read on these here internets. Numerous adjective-filled news stories have warned me that the "scary new Android malware" is "spreading quickly," targeting "millions" (millions!) of users, and occasionally even "kicking people square in the groin." (All right, so I made that last part up. But you get the idea.)
BUT WAIT! It gets worse: The malware, known as FluBot (because it wouldn't be Android malware if it didn't have an annoyingly cutesy name), works by showing up on your phone, gaining access to all of your most sensitive data, and then sending your deepest secrets to hooligans who are preemptively cackling over your unavoidable misfortune.
It's enough to make you want to toss your Android phone into the nearest quarry and go into permanent hiding. I get it — who wouldn't react that way? Before you start searching for the nearest bunker, though, there's something you should know about this menacing Android malware. And it's something that, if we're being fully honest, applies to the vast majority of fear-inducing Android security stories we see out in the wild.
Ready? This Android malware should be incredibly scary for you — if, that is, you're a complete and total nitwit.
No offense to the complete and total nitwits of the world (we love you, we really do), but let me provide a little oft-missing context about how exactly this latest big, bad malware monster actually works:
- Someone you don't know sends you a message with a link and a friendly suggestion that you tap it to install a program you've never heard of. (They might also offer you a lollipop and suggest you get into their unmarked van, but I haven't been able to confirm that yet.)
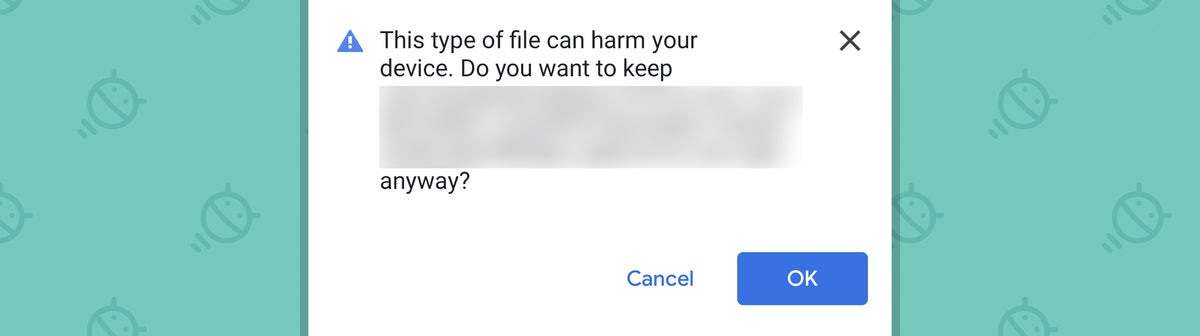
- If you tap the link, you'll get taken to a website that tries to download an Android program file — what's known as an APK file — onto your phone. That step would cause your phone to pop up a warning letting you know that the type of file involved could harm your device and asking if you're really, truly sure you want to continue.
 JR
JR- Should you disregard that warning and opt to march forward, the file would then get downloaded onto your device. At that point, it'd be up to you to tap a command to open it. Notably, nothing is happening automatically or without your active involvement at any point along the way here.
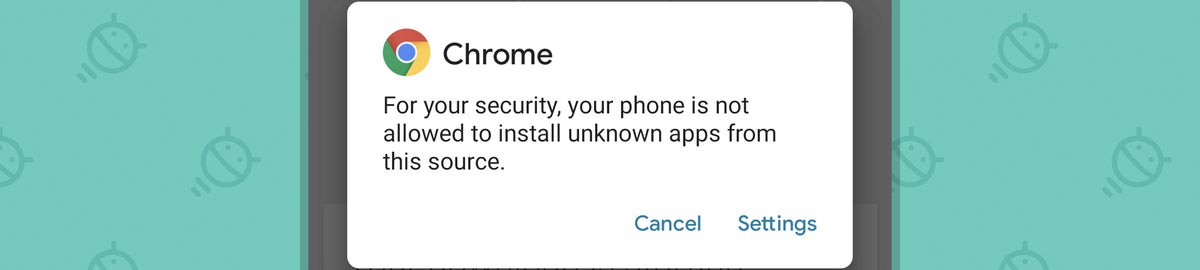
- If you tap the command to open the file, you'd then see a strongly worded warning informing you that for your security, your phone is not allowed to install unknown apps from this source.
 JR
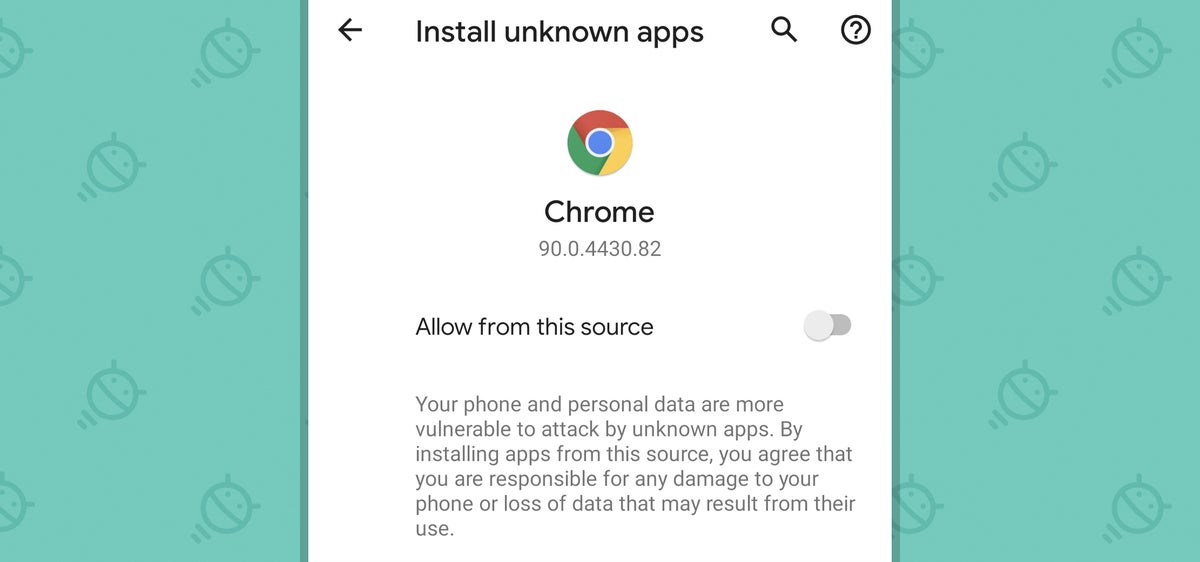
JR- In order to get around that, you'd have to tap the "Settings" link within the warning, after which you'd be taken to a screen that tells you your phone and personal data are "more vulnerable to attack by unknown apps" and confirming, again, that you really, truly want to continue.
 JR
JR- If you accept that warning and flip the switch to allow the app to be installed, you'll then get another confirmation prompt showing you the name of the app and asking, once more, if you really, truly want to install it.
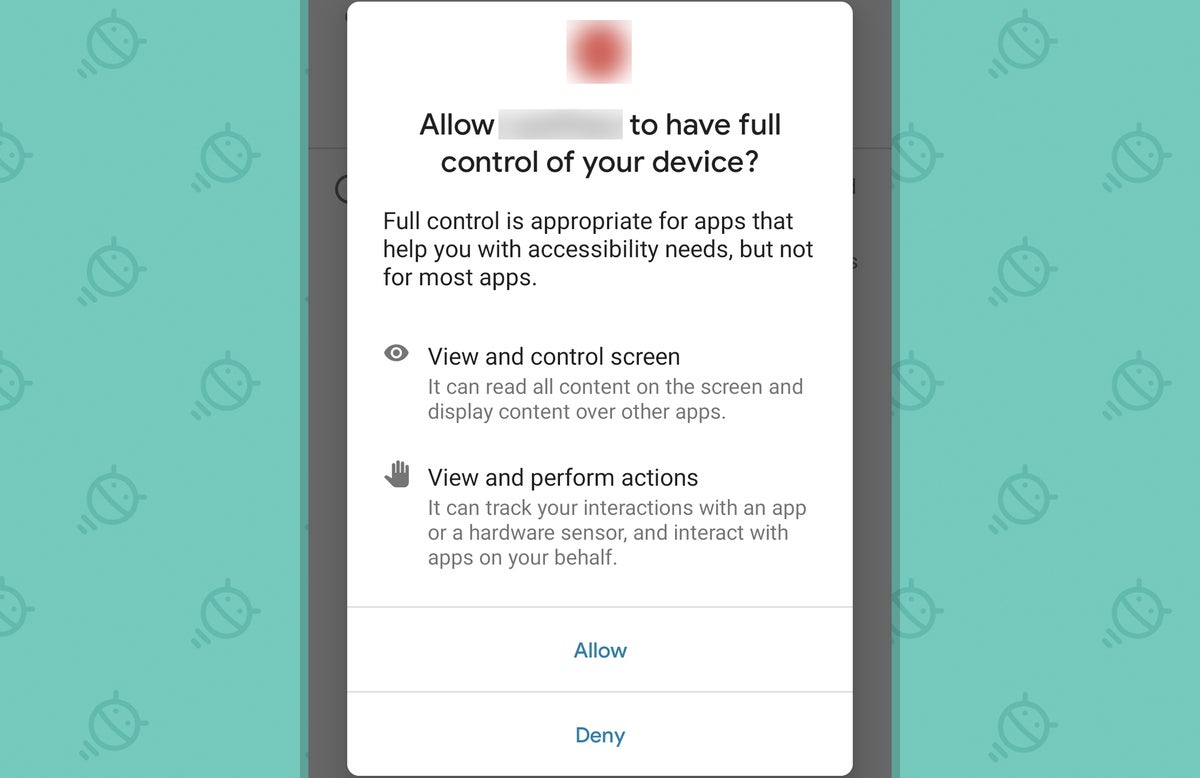
- If you make it through all of that and keep going, the app would then be installed on your phone! EEK! Hang on, though: Android apps can only access different types of data and system functions if you explicitly grant them the permissions to do so. In the case of this particular ne'er-do-weller, it sounds like it'd need to ask you for permission to send and manage SMS messages — as it taps into your messaging app in order to spread its link-love to other folks in your phone's contacts — along with the system accessibility service permission, which would empower a program to read anything on your screen and see what you're typing into fields like password prompts. That level of access is intended only for genuine accessibility-oriented services as well as apps like password managers that need it in order to operate, and the warning shown to you prior to activating it is extremely stern and clear about that fact.
 JR
JR- If you see it fit to allow the app those levels of access anyway — despite all the warnings and the fact that there's no logical reason why it'd need such access or why you should possibly do that — then yes, the app could then run on your phone and do what it came to do (although remember, it'd also need permission to access the internet before it could get your deepest secrets off of your device and send 'em to anyone else). At this point, congratulations: You have officially reached complete and total nitwit status.
In related news, if a suspicious-looking fella approaches you on the street and asks for your wallet — then tells you three different times what he'll be able to do if you give him your wallet and confirms four times that you actually want to give it to him, anyway — well, by golly, if you go ahead and hand him that wallet, some bad stuff is probably gonna happen.
All analogies aside, there's actually one more asterisk to this, and it's an important one: In an enterprise arrangement, any company whose IT department isn't made up entirely of complete and total nitwits would have policies preventing users from installing apps from random unknown sources in the first place. Such policies are in place by default on a managed Android enterprise arrangement, in fact, so the IT folk would've had to deliberately disable that form of protection in order for any of these hijinks to be possible on a company-connected phone.
Android enterprise policies can also control exactly which apps are allowed to be set as accessibility services, so there's another layer of nitwit protection. And that's to say nothing of the anti-phishing measures lots of companies also put in place on their devices. In virtually any (non-nitwit-involving) business situation, then, you'd never get past step 3 — or possibly even step 2 — no matter how hard you tried.
And even in an individual user situation, you'd really have to work pretty darn diligently to let an app like this do its dirty bidding, given all the barriers Android puts up before you could reach the point of actual danger.
And y'know what? It's more or less the same freakin' story every freakin' time. That's absolutely the case with another Android bogeyman making the rounds right now — a "sophisticated new malicious app" that "disguises itself as a System Update application" and steals "data, messages, [and] images" while simultaneously "taking control of Android phones" and monitoring everything from your phone call contents to your messages and even your browser history (yes, including that one site you looked at before bed last night).
But, oh yeah: You'd have to go to some random unofficial website to find and download the thing and then skate past all those same sorts of prompts to install it and give it the various forms of advanced access it needs to operate. And if you're using a work-connected phone, you probably couldn't do any of that, anyway.
Oh, and the company pushing the publicity campaign about that one, by the way? It's Zimperium, which conveniently and completely coincidentally happens to sell security software for Android devices. (Funny how that always seems to work out that way, isn't it?)
The bottom line is this, my fellow Android-carrying hominid: Android security can certainly seem scary on the surface, especially if you spend much time swimming in the endless stream of sensational stories about it. And goodness gracious, some weeks, those fear-infested waters can be damn-near impossible to avoid.
Once you start looking closely and asking the right questions, though, an Android security scare is almost always far less frightening than it initially appears. And despite what the companies pushing these narratives would presumably prefer, there's rarely any real reason to panic — so long as even the teensiest shred of common (non-complete-and-total-nitwit) sense is involved.
Sign up for my weekly newsletter to get more practical tips, personal recommendations, and plain-English perspective on the news that matters.

"Android" - Google News
April 29, 2021 at 08:38PM
https://ift.tt/3aQaGMR
A highly sarcastic Android security warning - Computerworld
"Android" - Google News
https://ift.tt/336ZsND
https://ift.tt/2KSW0PQ
Bagikan Berita Ini














0 Response to "A highly sarcastic Android security warning - Computerworld"
Post a Comment